Table of Contents
Consul cluster 구성하기
폴더 생성
mkdir consul_server_cluster
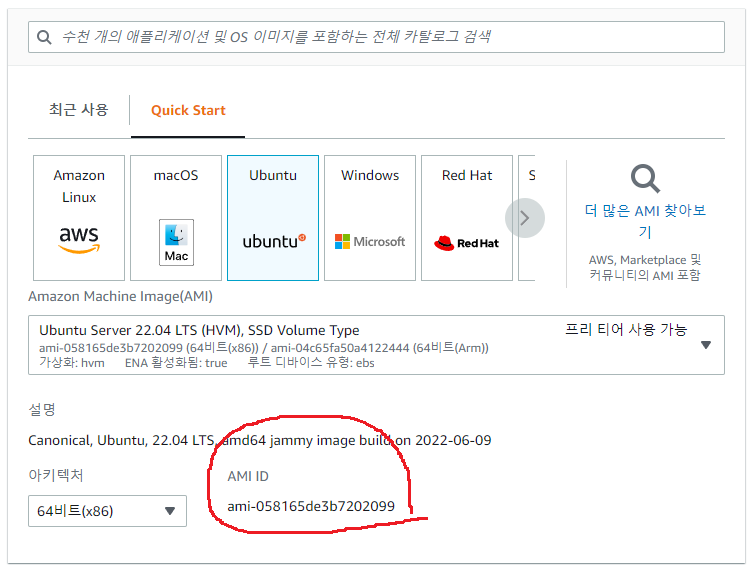
cd consul_server_clusterAMI 아이디 찾기
AMI 아이디는 아래처럼 찾을 수 있습니다.
변수설정 및 서버 실행
vi variables.tf
-----------------------------
variable "stack_name" {
description = "The name to prefix onto resources."
type = string
default = "my"
}
variable "owner_name" {
description = "Your name so resources can be easily assigned."
type = string
default = "skyer9"
}
variable "owner_email" {
description = "Your email so you can be contacted about resources."
type = string
default = "skyer9@gmail.com"
}
variable "region" {
description = "The AWS region to deploy into."
type = string
default = "ap-northeast-2"
}
variable "availability_zones" {
description = "The AWS region AZs to deploy into."
type = list(string)
default = ["ap-northeast-2a", "ap-northeast-2b", "ap-northeast-2c"]
}
variable "ami" {
description = "The AMI to use, preferably built by the supplied Packer scripts."
type = string
default = "ami-0ea5eb4b05645aa8a"
}
variable "consul_server_instance_type" {
description = "The EC2 instance type to launch for Consul servers."
type = string
default = "t3a.micro"
}
variable "server_instance_type" {
description = "The EC2 instance type to launch for Nomad servers."
type = string
default = "t3a.micro"
}
variable "client_instance_type" {
description = "The EC2 instance type to launch for Nomad clients."
type = string
default = "t3a.small"
}
variable "consul_server_count" {
description = "The number of Consul servers to run."
type = number
default = 1
}
variable "server_count" {
description = "The number of Nomad servers to run."
type = number
default = 1
}
variable "client_count" {
description = "The number of Nomad clients to run."
type = number
default = 1
}
variable "root_block_device_size" {
description = "The number of GB to assign as a block device on instances."
type = number
default = 8
}
variable "retry_join" {
description = "The retry join configuration to use."
type = string
default = "provider=aws tag_key=ConsulAutoJoin tag_value=auto-join"
}
variable "allowlist_ip" {
description = "A list of IP address to grant access via the LBs."
type = list(string)
default = ["0.0.0.0/0"]
}
variable "access_key" {
description = "AWS_ACCESS_KEY_ID"
type = string
default = "XXXXXXXXXXXXXXX"
}
variable "secret_access_key" {
description = "AWS_SECRET_ACCESS_KEY"
type = string
default = "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
}
-----------------------------vi main.tf
-----------------------------
provider "aws" {
region = var.region
}
resource "aws_instance" "consul_server" {
ami = var.ami
instance_type = var.consul_server_instance_type
// key_name = var.key_name
// vpc_security_group_ids = [aws_security_group.consul_lb.id]
count = var.consul_server_count
// iam_instance_profile = aws_iam_instance_profile.consul_server.name
tags = {
Name = "${var.stack_name}-consul_server-${count.index + 1}"
ConsulAutoJoin = "auto-join"
OwnerName = var.owner_name
OwnerEmail = var.owner_email
}
root_block_device {
volume_type = "gp2"
volume_size = var.root_block_device_size
delete_on_termination = "true"
}
// user_data = data.template_file.user_data_consul_server.rendered
}
-----------------------------terraform init
terraform validate
terraform plan테스트로 인스턴스를 생성해 봅니다.
현재상태에서는 아무런 기능도 없고,
단지 EC2 인스턴스를 생성해 보고 삭제합니다.
terraform apply
terraform show
terraform destroy권한설정
vi private.tf
-----------------------------
variable "key_name" {
description = "The EC2 key pair to use for EC2 instance SSH access."
type = string
default = "aws_key" # 내 키페어
}
variable "my_ip" {
description = "A list of IP address to grant access via the LBs."
type = list(string)
default = ["183.101.XXX.XXX/32"] # 내 아이피
}
-----------------------------vi sg.tf
-----------------------------
data "aws_vpc" "default" {
default = true
}
resource "aws_security_group" "consul_lb" {
name = "${var.stack_name}-consul-lb"
vpc_id = data.aws_vpc.default.id
# Consul HTTP API & UI.
ingress {
from_port = 8300
to_port = 8600
protocol = "tcp"
cidr_blocks = var.my_ip
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = var.my_ip
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_security_group_rule" "consul_to_consul_ingress" {
type = "ingress"
from_port = 1
to_port = 65535
protocol = "tcp"
security_group_id = aws_security_group.consul_lb.id
source_security_group_id = aws_security_group.consul_lb.id
}
-----------------------------vi iam.tf
-----------------------------
resource "aws_iam_instance_profile" "consul_server" {
name_prefix = var.stack_name
role = aws_iam_role.consul_server.name
}
resource "aws_iam_role" "consul_server" {
name_prefix = var.stack_name
assume_role_policy = data.aws_iam_policy_document.consul_server_assume.json
}
resource "aws_iam_role_policy" "consul_server" {
name = "nomad-server"
role = aws_iam_role.consul_server.id
policy = data.aws_iam_policy_document.consul_server.json
}
data "aws_iam_policy_document" "consul_server_assume" {
statement {
effect = "Allow"
actions = ["sts:AssumeRole"]
principals {
type = "Service"
identifiers = ["ec2.amazonaws.com"]
}
}
}
data "aws_iam_policy_document" "consul_server" {
statement {
effect = "Allow"
actions = [
"ec2:DescribeInstances",
"ec2:DescribeTags",
]
resources = ["*"]
}
}
-----------------------------vi main.tf
-----------------------------
resource "aws_instance" "consul_server" {
// ......
key_name = var.key_name
vpc_security_group_ids = [aws_security_group.consul_lb.id]
iam_instance_profile = aws_iam_instance_profile.consul_server.name
// ......
-----------------------------다시 인스턴스를 생성해 봅니다.
하지만 아직 Consul 서버로서 기능하지는 않습니다.
terraform validate
terraform plan
terraform apply
terraform show
terraform destroyConsul server 설정
mkdir files
vi files/user-data-consul-server.sh
-----------------------------
#!/bin/bash
set -e
sudo mkdir -p /ops
cd /ops/
sudo wget https://github.com/skyer9/TerraformOnAws/raw/main/files/setup.sh
sudo wget https://github.com/skyer9/TerraformOnAws/raw/main/files/net.sh
sudo wget https://github.com/skyer9/TerraformOnAws/raw/main/files/consul-server.sh
sudo wget https://github.com/skyer9/TerraformOnAws/raw/main/files/consul-server.hcl
sudo wget https://github.com/skyer9/TerraformOnAws/raw/main/files/consul.service
sudo chmod +x /ops/setup.sh
sudo chmod +x /ops/net.sh
sudo chmod +x /ops/consul-server.sh
sudo bash -c "/ops/consul-server.sh \"${server_count}\" \"${retry_join}\""
# rm -rf /ops/
-----------------------------vi templates.tf
-----------------------------
data "template_file" "user_data_consul_server" {
template = file("${path.module}/files/user-data-consul-server.sh")
vars = {
server_count = var.consul_server_count
region = var.region
retry_join = var.retry_join
}
}
-----------------------------vi main.tf
-----------------------------
resource "aws_instance" "consul_server" {
// ......
user_data = data.template_file.user_data_consul_server.rendered
}
-----------------------------terraform init -upgrade
terraform apply
terraform show
terraform destroyhttp://<서버 아이피>:8500/ 에 접속하여 확인할 수 있습니다.